Secure Access, Compliance & Workforce Monitoring for Telecom Providers
Telecom firms must protect customer data and critical infrastructure. RemoteDesk secures remote access, monitors activity, and ensures compliance for distributed teams.
The fastest-growing companies use RemoteDesk.
Challenges
RemoteDesk Capabilities for Telecom Providers
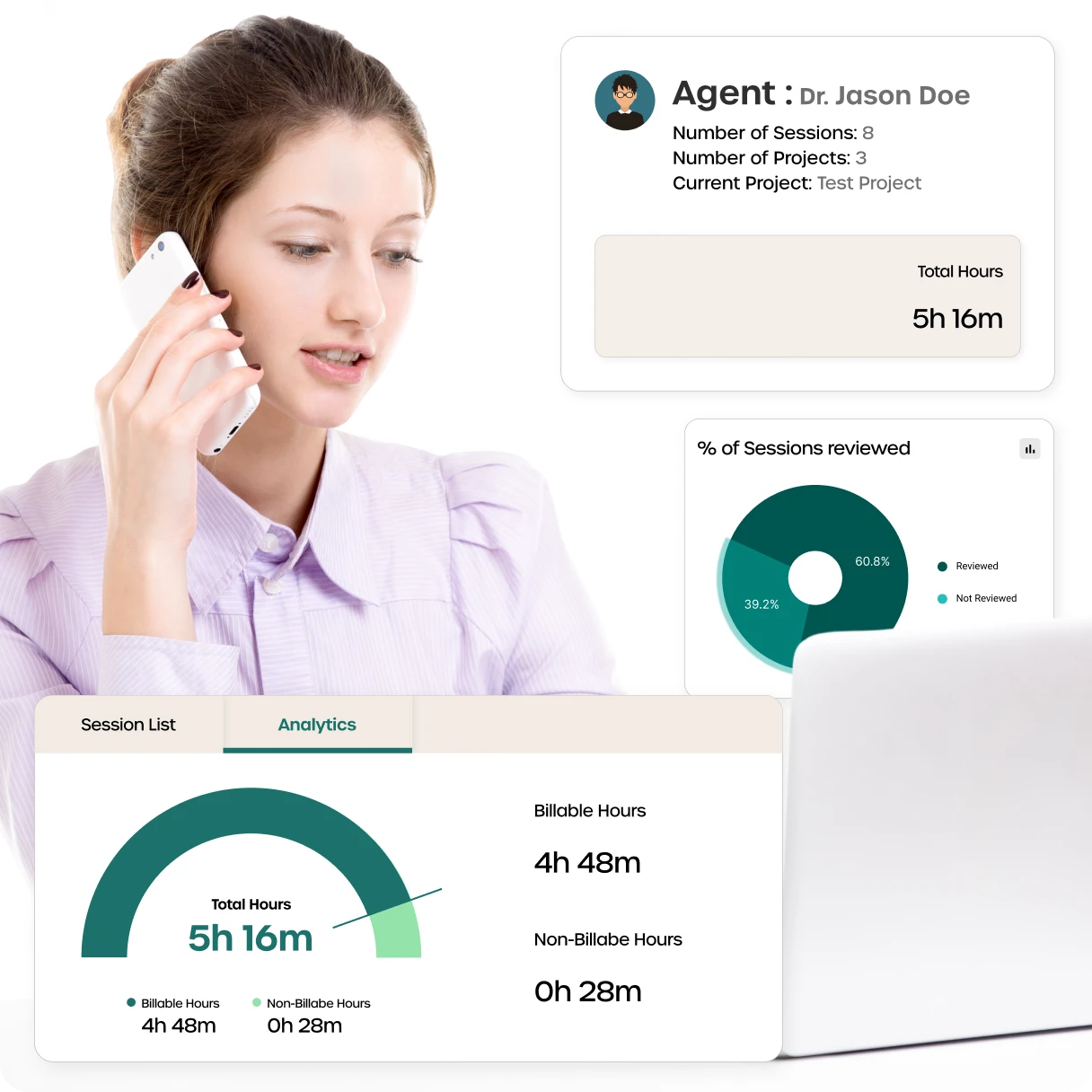
Advance Workforce Monitoring
RemoteDesk tracks real-time session activity to ensure policy-compliant environments and secure operations.
● Unauthorized mobile
● Mirroring detection
● Suspicious user behavior or inactive sessions
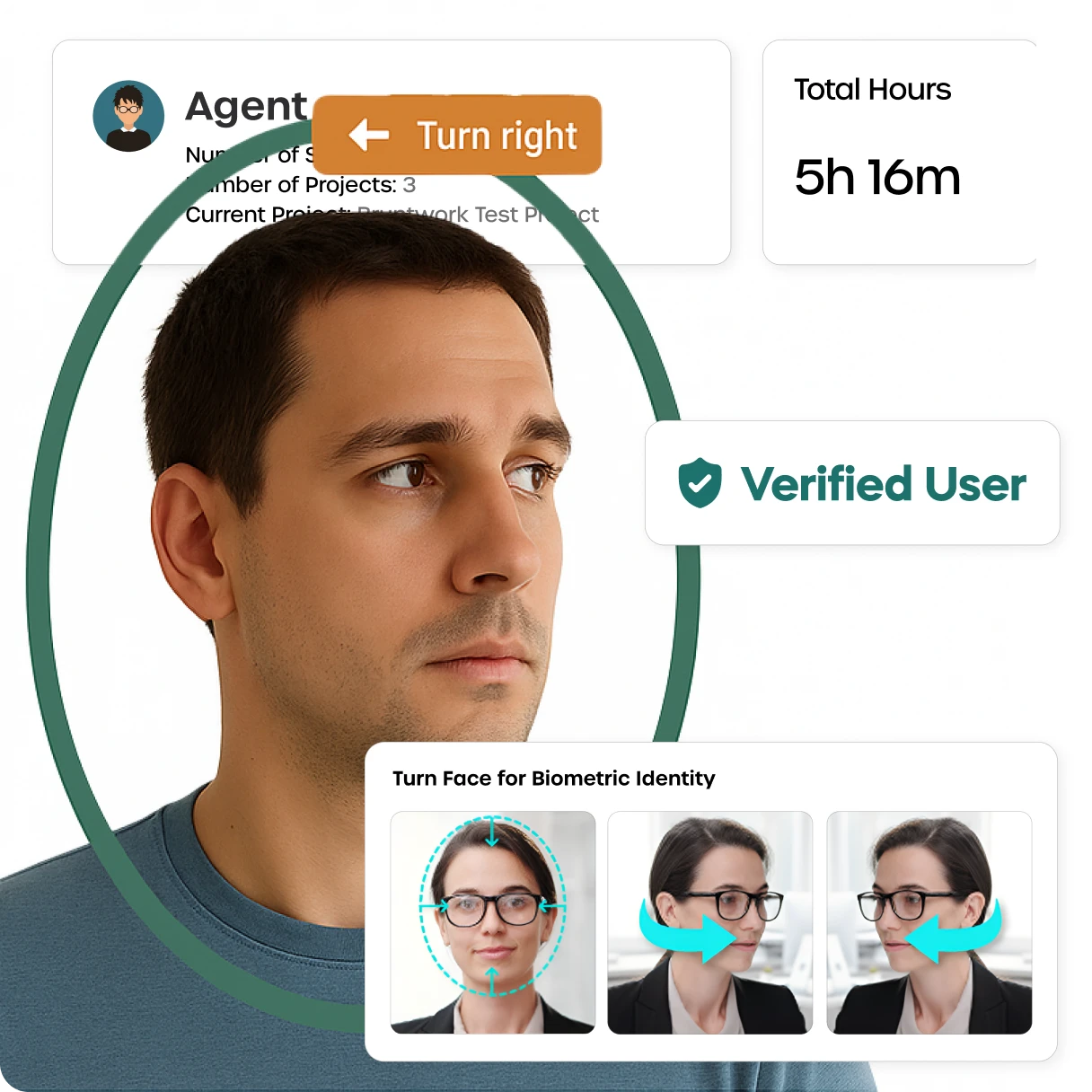
FaceAuth Continuous Verification
FaceAuth confirms identity throughout each session, not just at login.
● Detects session hijacking and impersonation
● Locks out unauthorized users
● Validates telecom staff presence during high-risk operations
Data Protection & Leak Prevention
RemoteDesk secures sensitive customer data, configurations, and network files.
● Prevents screen captures and screenshots
● Monitors for social engineering indicators
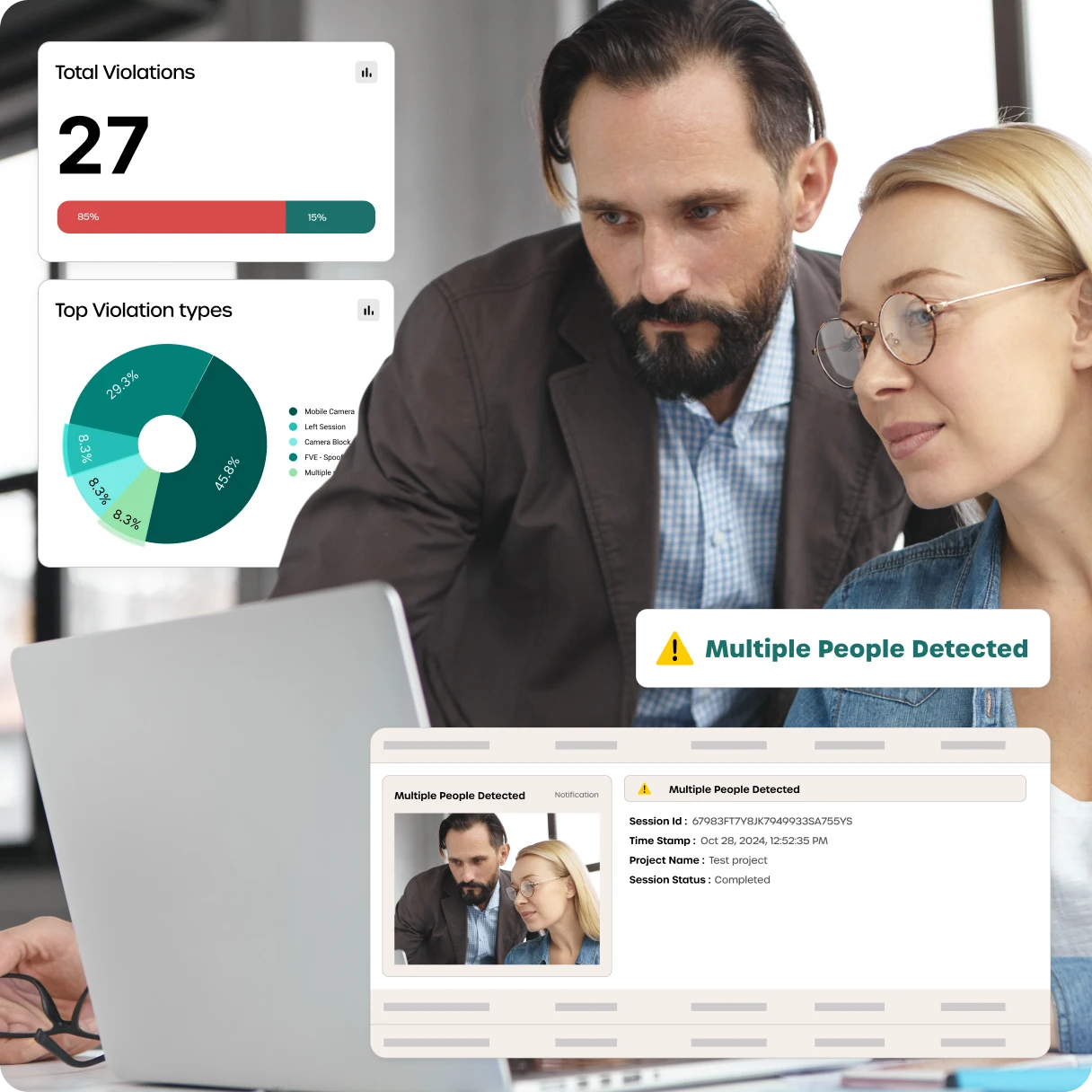
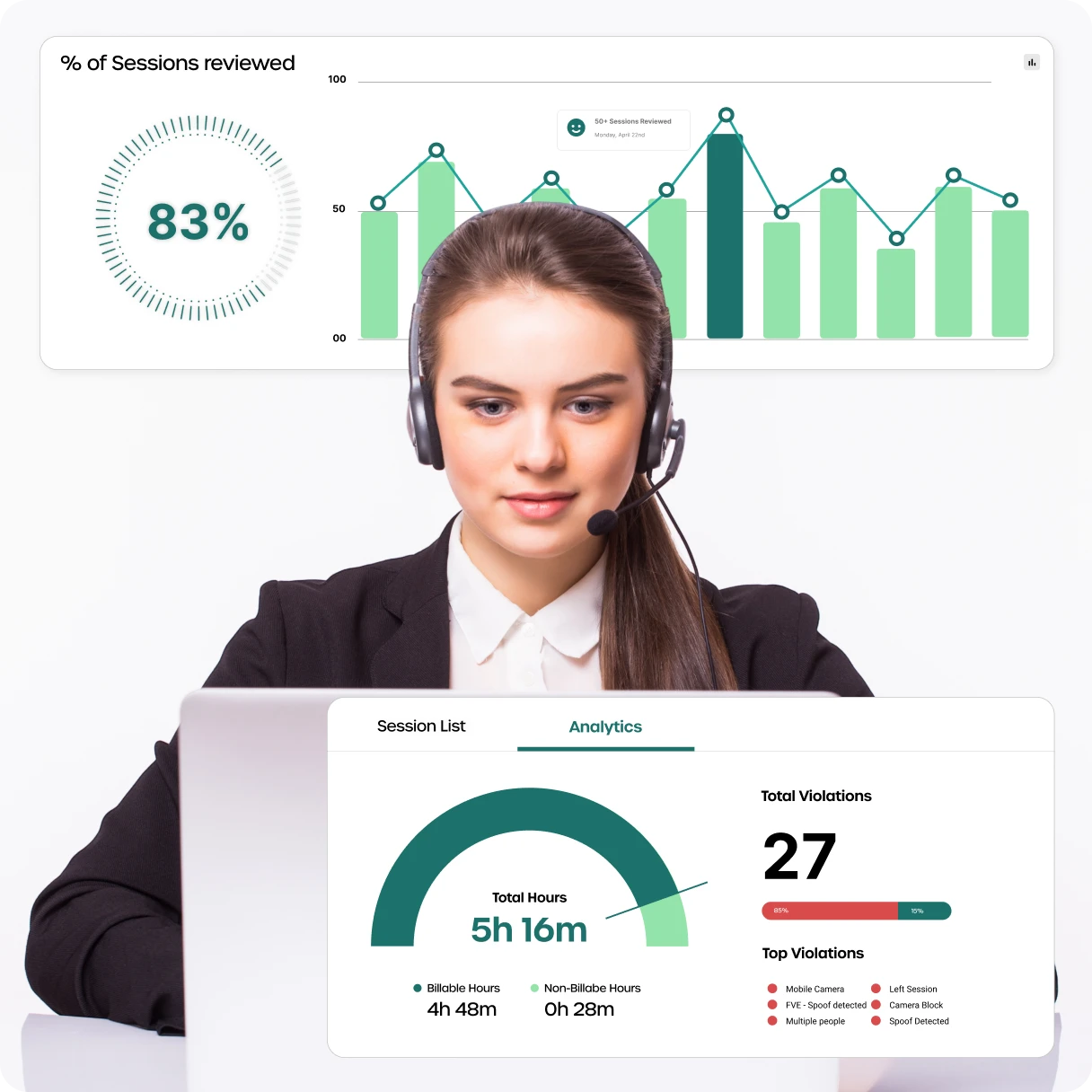
Violation Management Dashboard
Incidents are logged, categorized, and visualized in an admin dashboard.
● Role-based policy enforcement
● Time-stamped logs with screenshot evidence
● Custom alerts aligned with telecom security frameworks
Cost of Data Breaches in Telecom & Communication
RemoteDesk is designed to make your work life easier and more efficient.
$6.3M
Average cost of telecom breaches from exposed customer data and infrastructure risks.
70%
Telecoms operating hybrid work models, creating a larger surface area for insider threats.
49%
Cyberattacks in telecom stem from social engineering or compromised remote access credentials.
For Workforce
How RemoteDesk Safeguards Telecom Operations
Continuous Identity Verification
Ensure only verified telecom staff access CRM, billing systems, and network controls.
View on mapsContinuous Identity Verification
Ensure only verified telecom staff access CRM, billing systems, and network controls.
View on mapsContinuous Identity Verification
Ensure only verified telecom staff access CRM, billing systems, and network controls.
View on mapsKnow More
Frequently asked questions
Everything you need to know about the product and billing.
-
Q1: How does RemoteDesk help telecom companies maintain compliance?
RemoteDesk ensures compliance by monitoring sessions, validating identities, enforcing clean desk policy, and generating detailed logs aligned with telecom regulatory frameworks.
-
Q2: Can RemoteDesk detect unauthorized access to computer systems?
Yes. RemoteDesk continuously monitors user activity, detects impersonation attempts, and blocks unauthorized changes in real-time.
-
Q3: How does FaceAuth prevent identity fraud during remote work?
FaceAuth uses biometric facial recognition to verify telecom employees’ identity throughout the session, preventing session hijacking or unauthorized access.
-
Q4: Can RemoteDesk secure both on-premise and cloud-based telecom tools?
Absolutely. RemoteDesk operates across cloud, hybrid, or on-premise platforms to ensure consistent enforcement of security policies.
-
Q5: How quickly does RemoteDesk alert the admin about a policy violation?
Alerts are triggered in real time, allowing security teams to respond immediately to risky behavior or breaches.
Get Started Today
Sign up in minutes. Secure your remote
workforce with confidence.
See how RemoteDesk makes compliance and data protection effortless.