
Real-Time Enhanced Data Loss Protection
Prevent data breaches before they start. Secure eDLP uses computer vision monitoring and behavior analytics to automatically block insider threats, unauthorized access, and sensitive data leaks.

The fastest-growing companies use RemoteDesk.
Key Features
Enterprise Grade Data Protection & Compliance

Real-Time Face Verification
We use computer vision to continuously verify user identity through powered facial recognition ensuring that the right person is working at all times, preventing impersonation.

Enforces clean desk policies
Maintain a secure remote work environment by automatically detecting visual policy breaches like mobile phone use, or additional screens, enforcing "clean desk" policies.

Compliance Assurance
Generate time stamped user logs, evidence images and detailed activity reports to simplify compliance with standards like HIPAA, GDPR, PCI DSS, and ISO 27001.

Mobile on-device Data Protection
Receive alerts for policy violations related to mobile device usage ensuring no data is compromised via smartphone or tablet camera.

Proactive Threat Detection
We detect suspicious behavior and enforces security protocols to prevent data leaks before they happen reducing insider threats.

Imposter and spoof detection
We ensure identity integrity with technology that detects spoofing attempts, deepfakes, and other impersonation tactics.
Benefits
Who Benefits from
Secure eDLP?
Secure eDLP is essential for organizations handling sensitive data across distributed teams—especially those operating under strict regulatory and compliance requirements.
Perfect for:
Outsourcing & BPO Firms
Financial Institutions & FinTech
Healthcare Providers & MedTech
Legal, Consulting & IP-Driven Firms
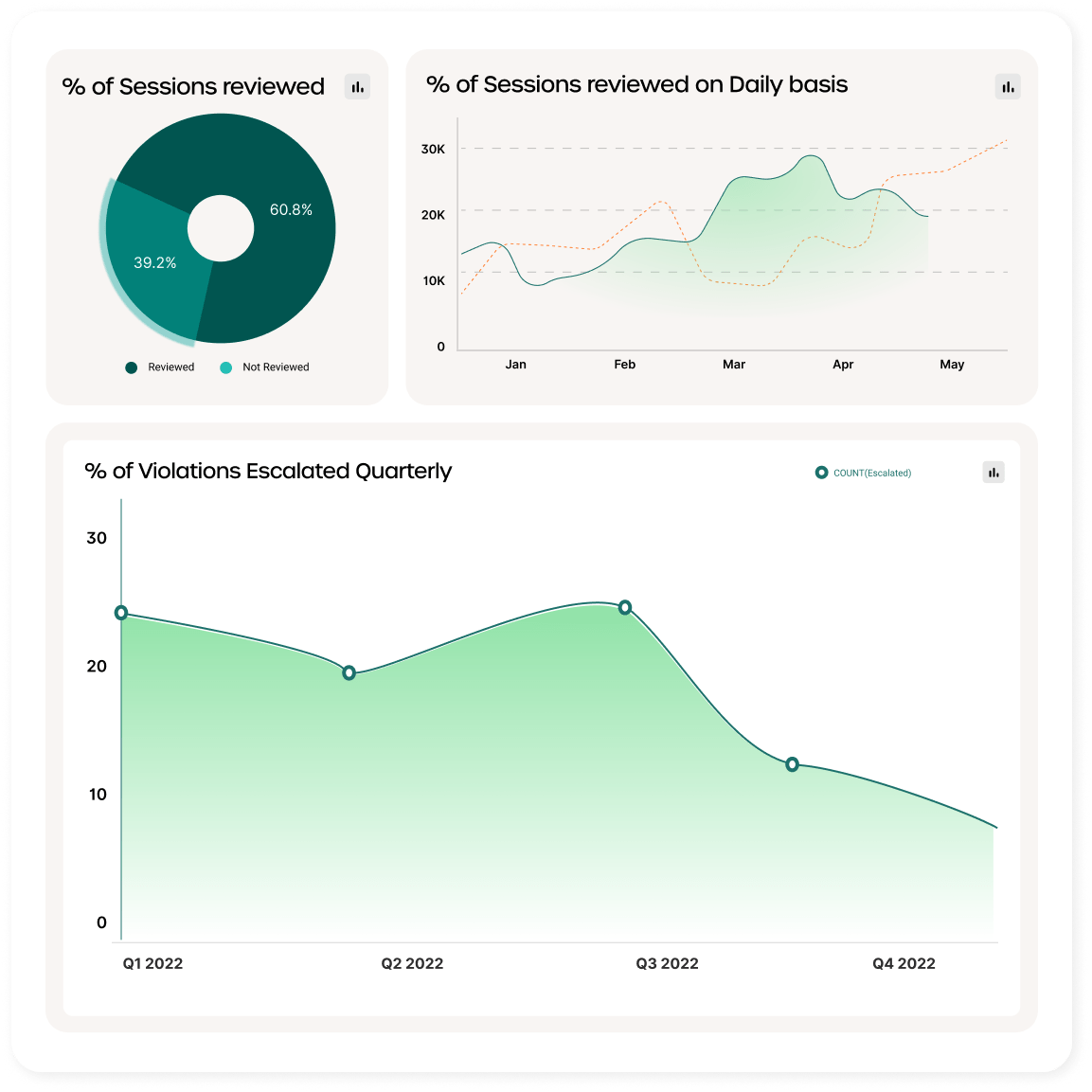
Secure
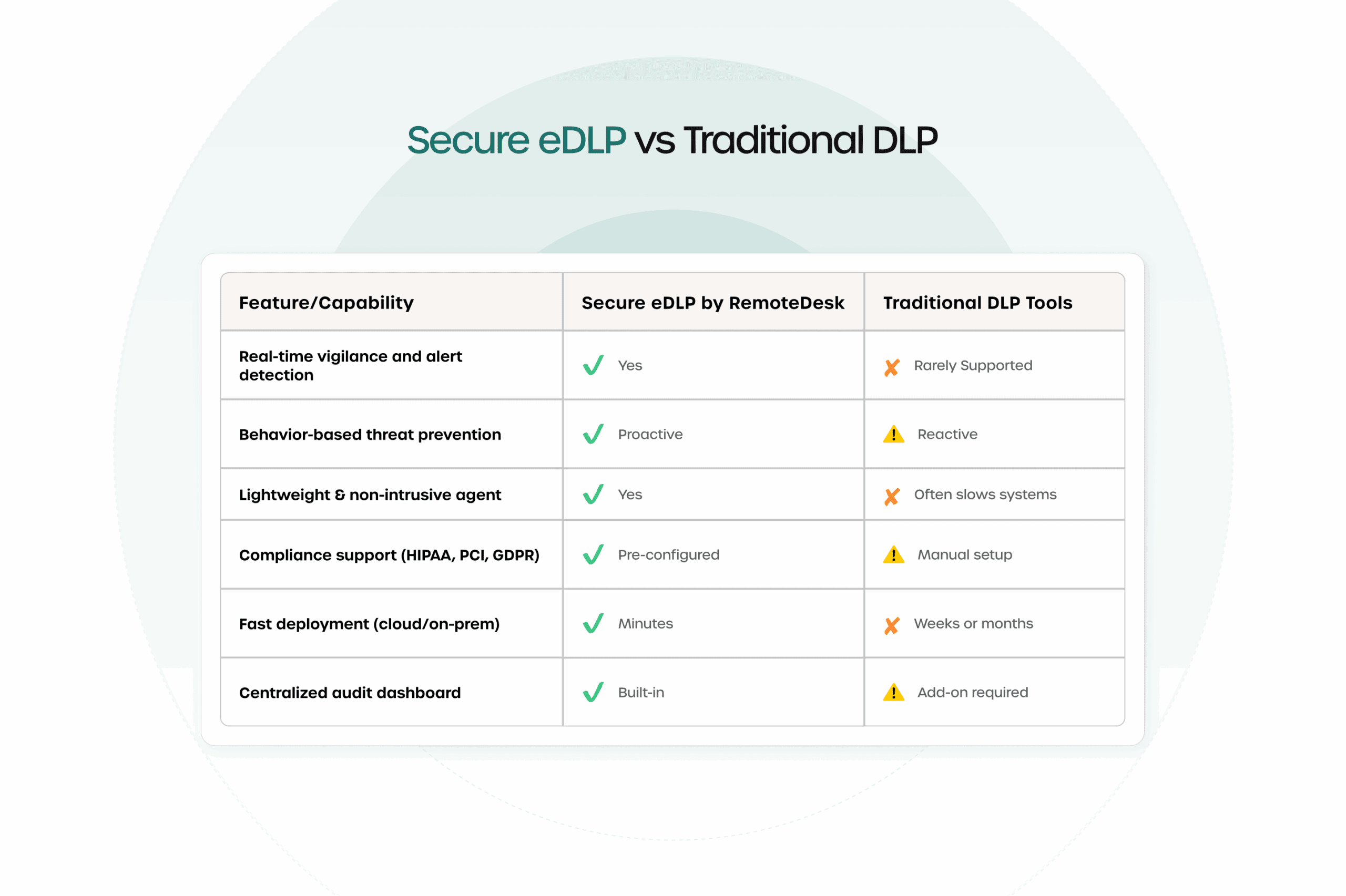
How Secure eDPL Works
Secure eDLP operates by continuously monitoring the work environment, utilizing face and ID verification to ensure that only authorized personnel have access. It detects potential violations, such as the presence of mobile devices, and sends instant alerts for any non-compliance.
Agent Installation
Deploy lightweight Secure eDLP agents to all endpoints (Windows/macOS).
Real-Time Monitoring
Continuously monitors user activity, and application usage.
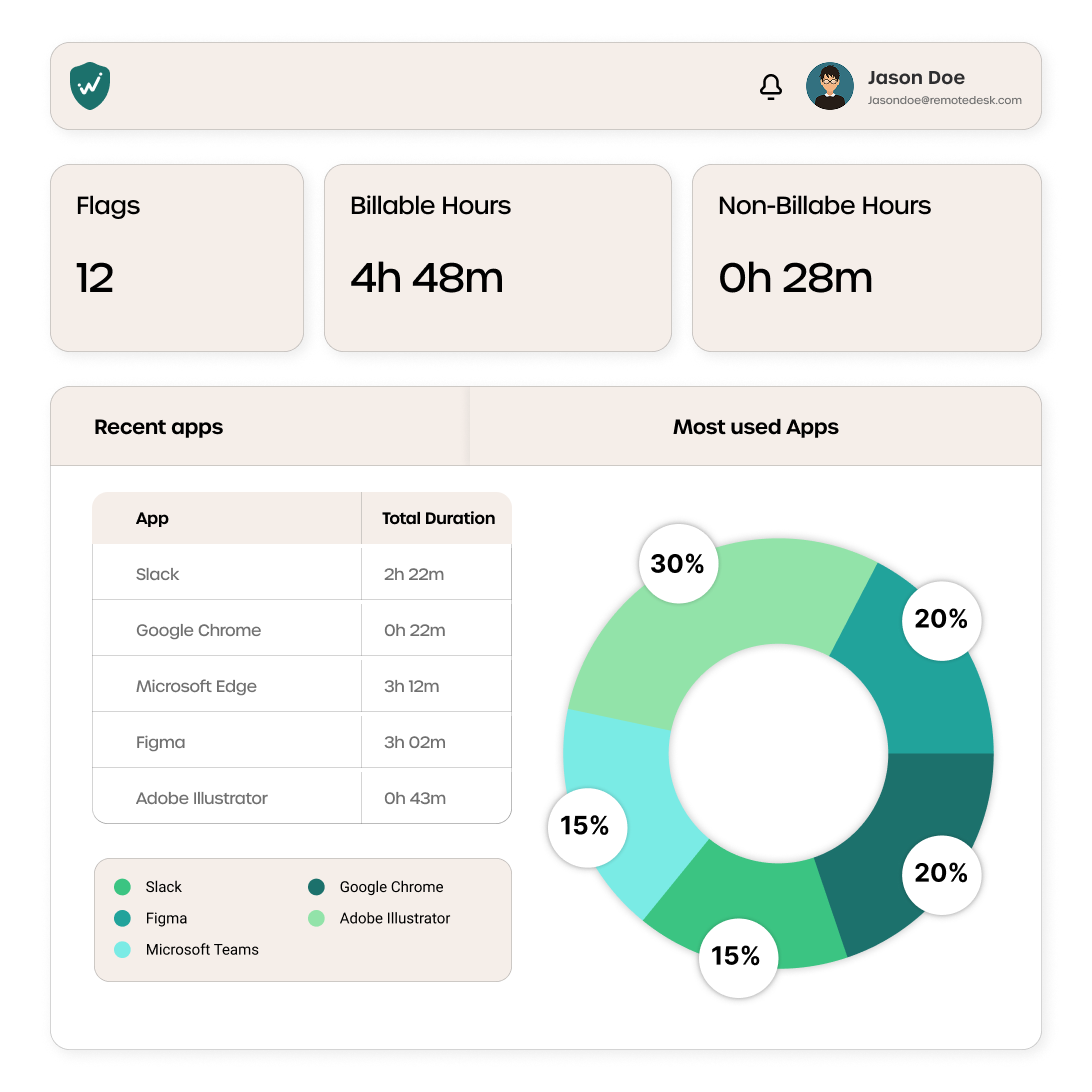
Insider Threat Detection
Identifies suspicious actions like:
¤ Unauthorized apps or browsers
¤ Print commands or screenshots
¤ Session hijacking or impersonation attempts
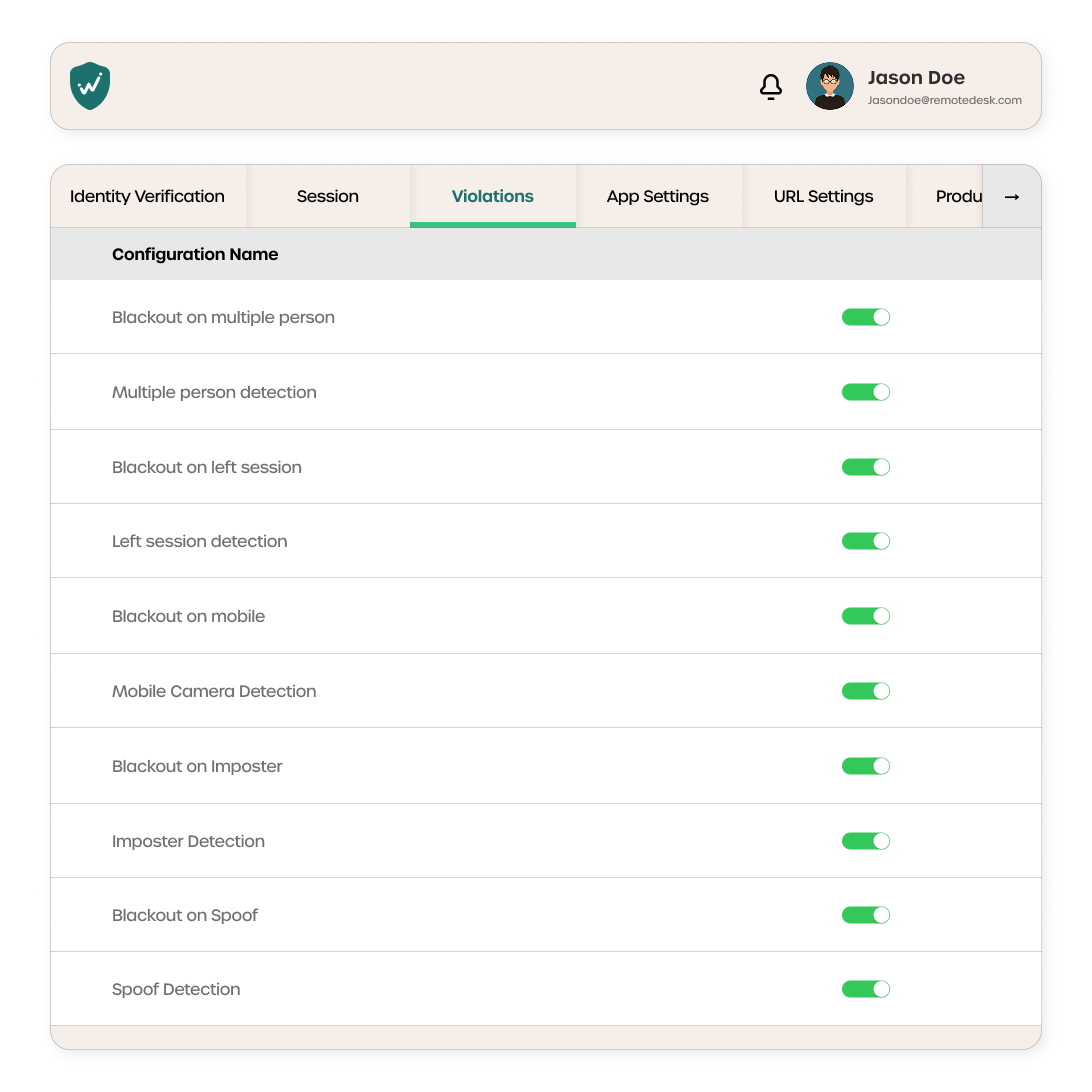
Instant Policy Enforcement
Automatically blocks the action, alerts the admin, and records evidence.
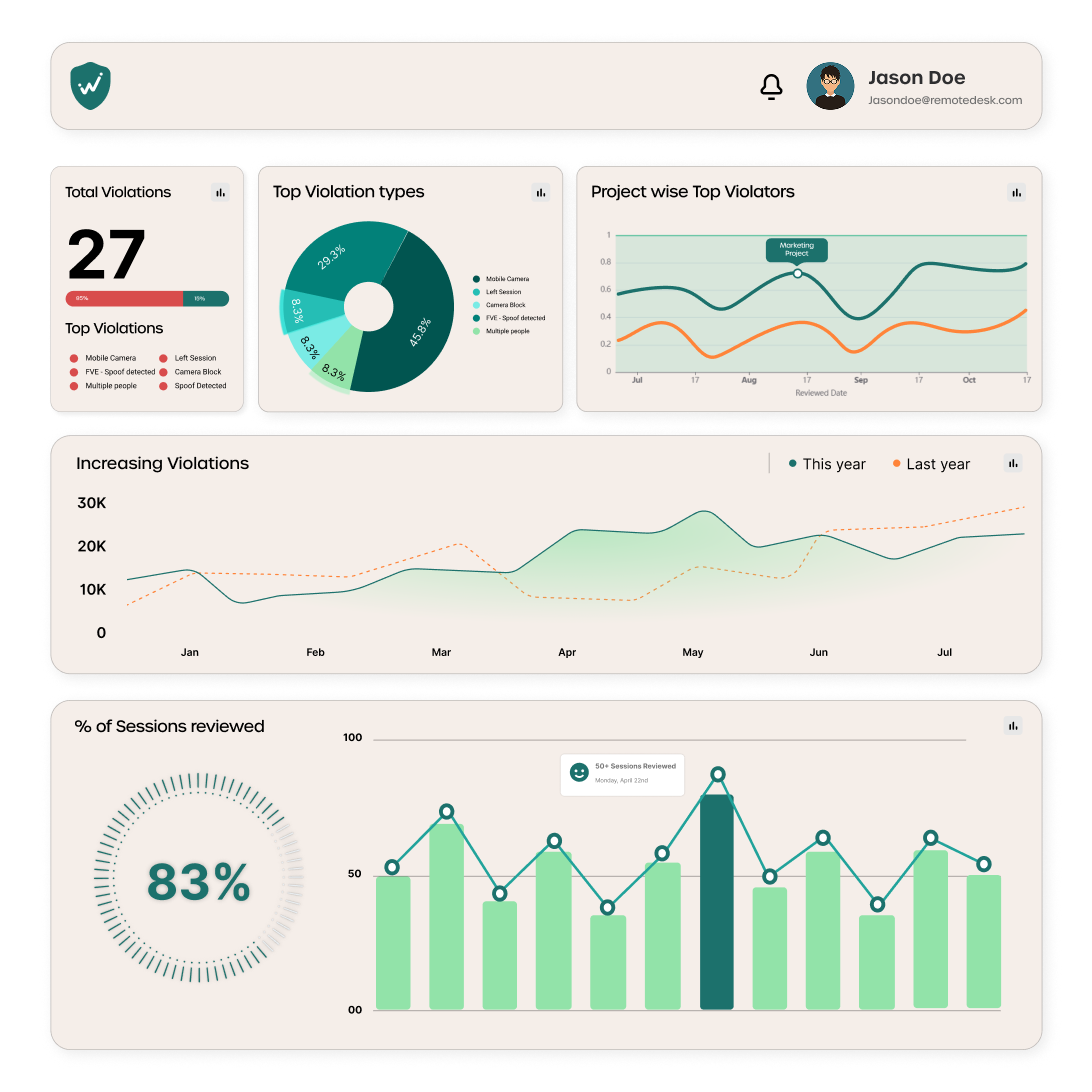
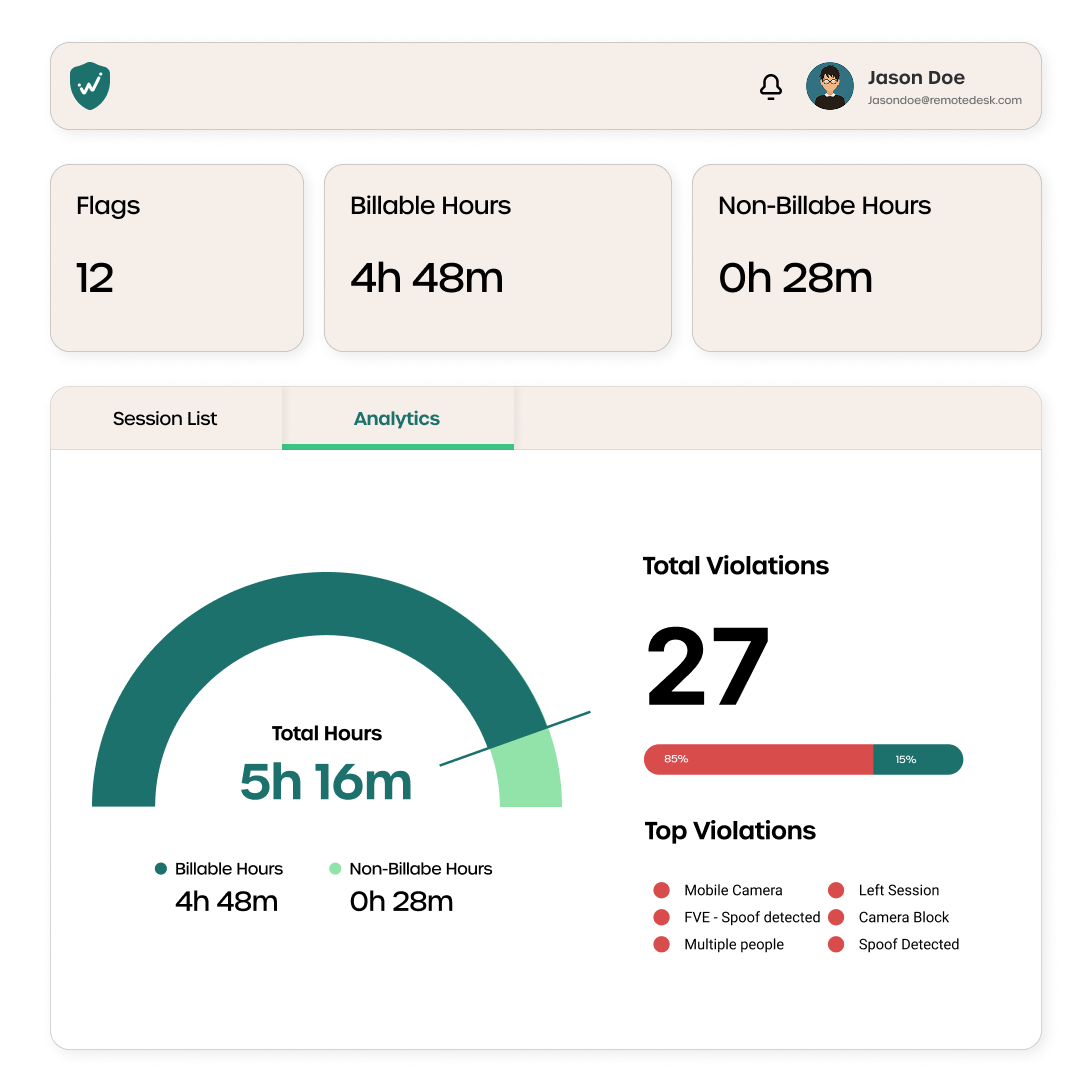
Centralized Dashboard
Admins view violations, reports, and compliance logs—ready for audits and internal reviews.
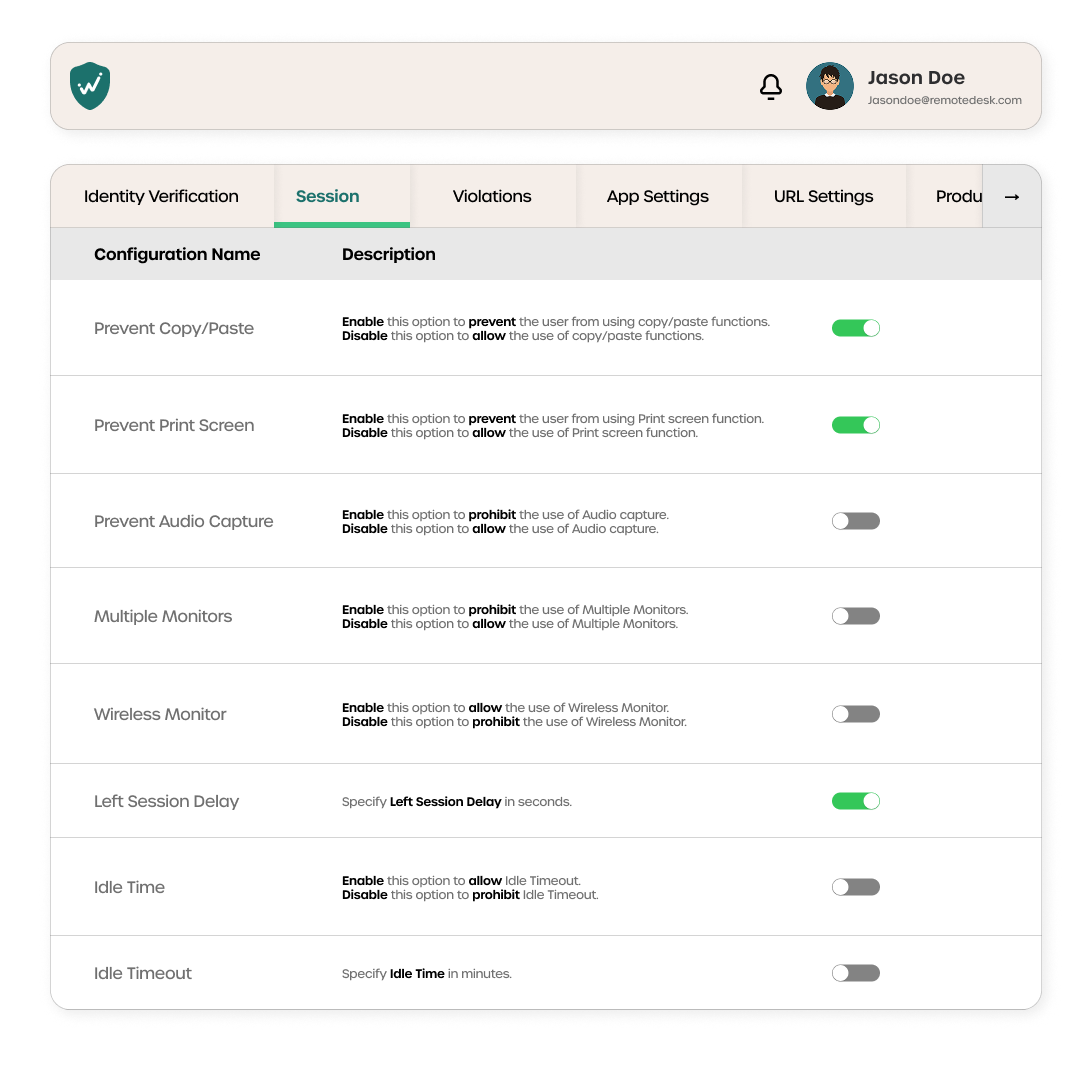
Customizable Policies
Enforce rules by role, department, location, or project with built-in support for major regulations.
What RemoteDesk
Offers You
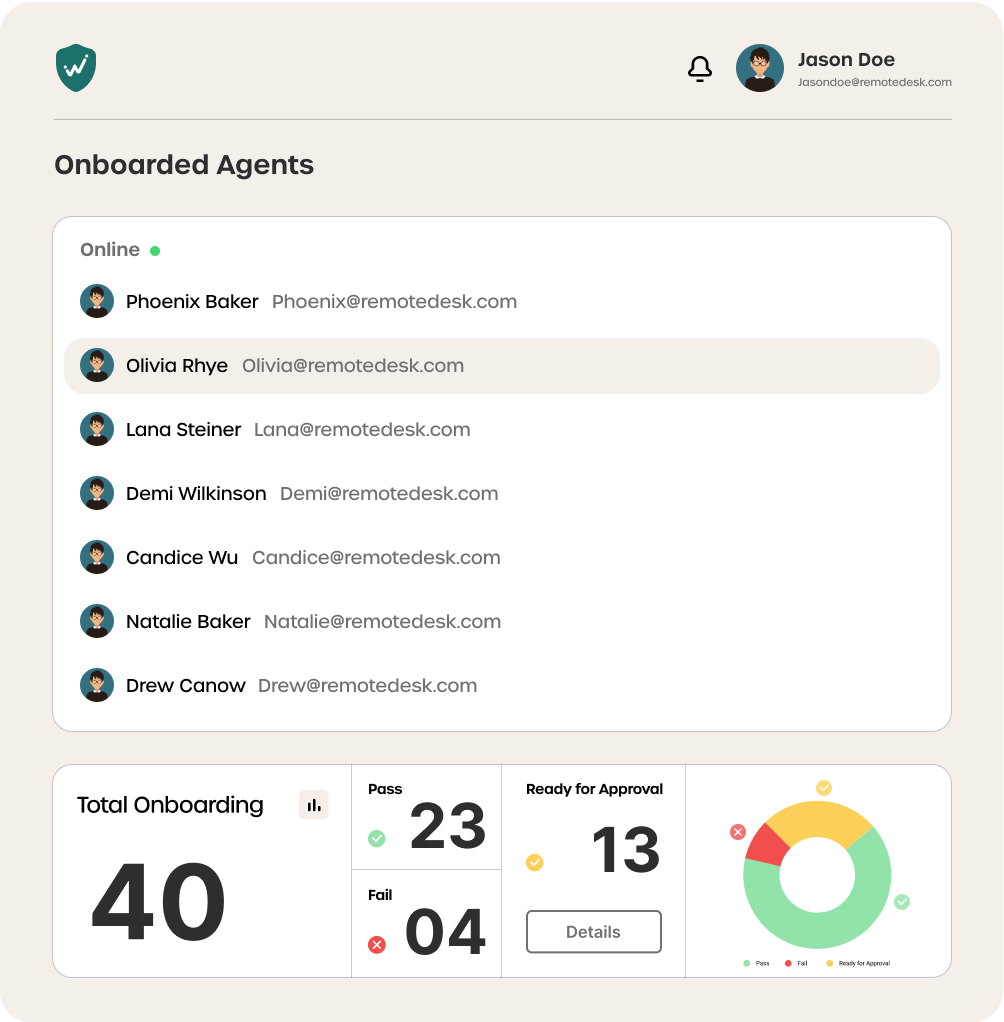
Advantage
Why Choose Secure eDLP
As remote and hybrid work environments grow, so do the risks of data breaches and insider threats. Traditional security tools fall short in providing real-time protection across distributed endpoints. Enhanced Data Loss Protection (eDLP) from RemoteDesk fills this gap by combining monitoring with policy-based controls to:
- Protect sensitive data across remote devices
- Prevent unauthorized sharing or access in real-time
- Ensure compliance with industry regulations
- Maintain user privacy while enforcing security
Use Cases
Protect Your Business & Data with Smart Security Features
Powering secure, compliant, and accountable remote work across every scenario
Safeguarding research, trials & patents
The client was scaling remote research teams globally and needed to prevent internal leaks of sensitive R&D files, formula data, and clinical trial records—all while staying compliant with compliance standards.
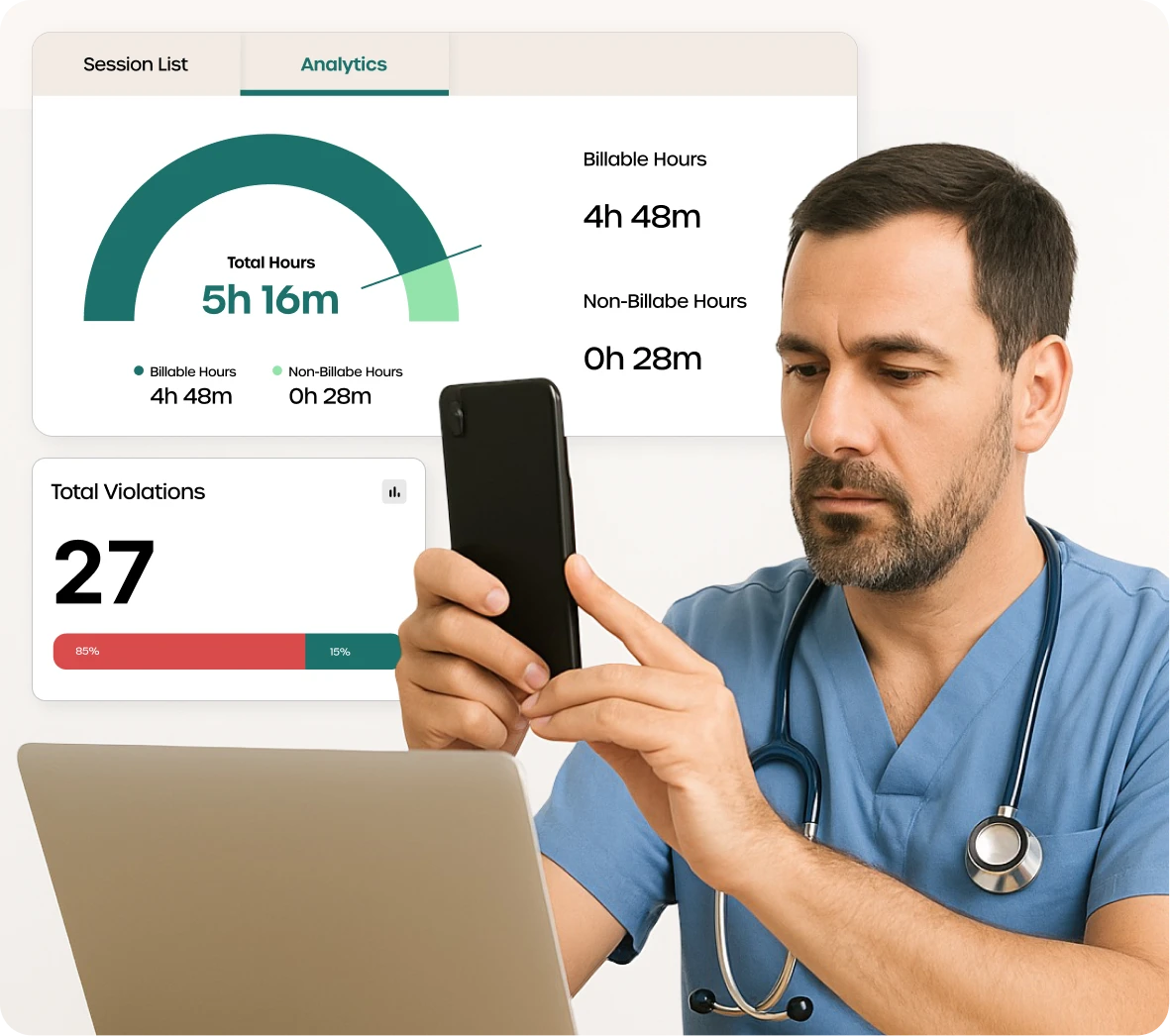
Protecting transactions & customer logs
The client needed robust controls to monitor employee devices and prevent misuse of customer payment details and behavior data—while maintaining SOC 2 and ISO 27001 compliance.
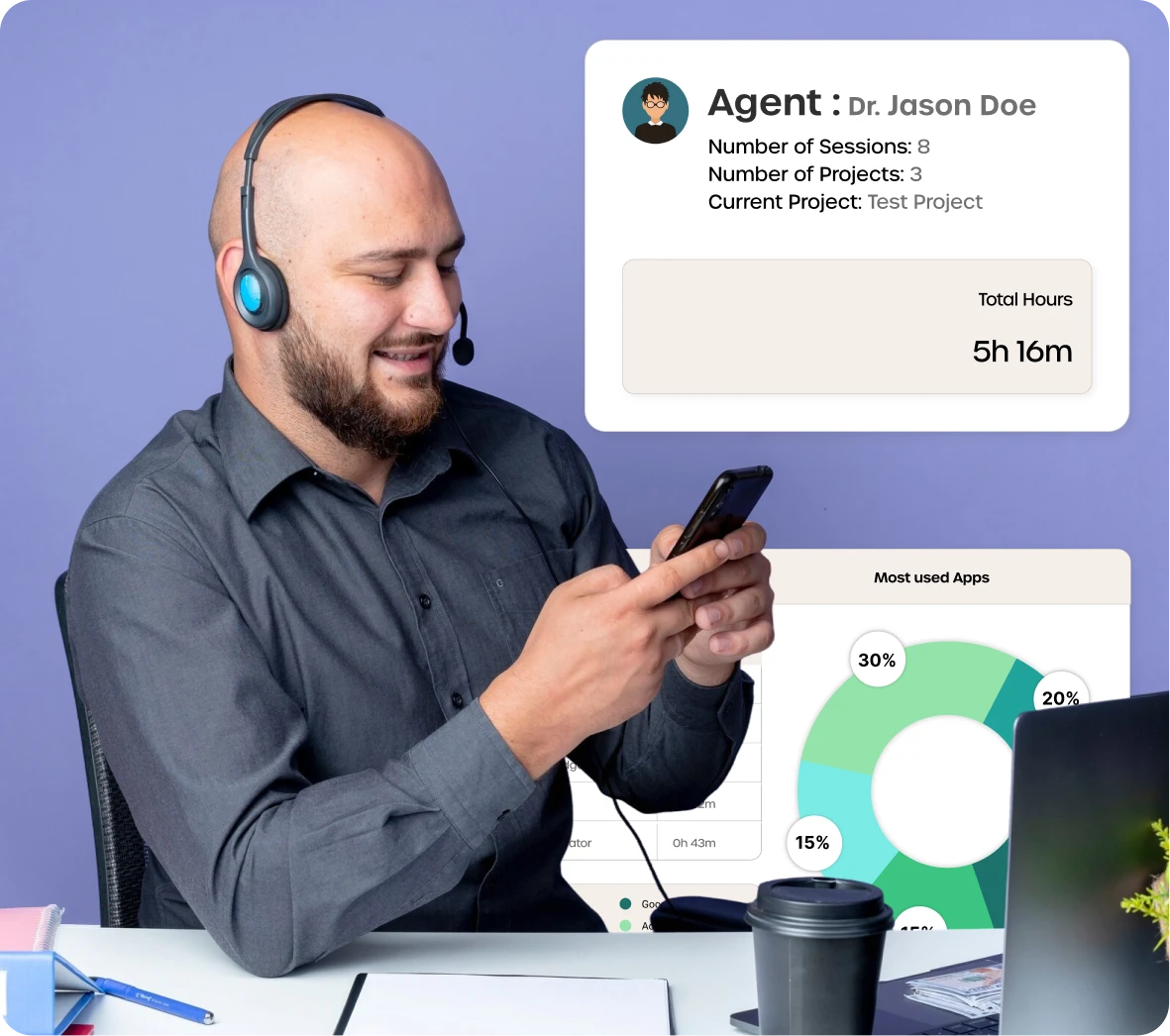
Securing unreleased digital assets
The client struggled to protect unreleased films and campaigns shared across remote editors, risking costly leaks and copyright issues due to unsecured file sharing.
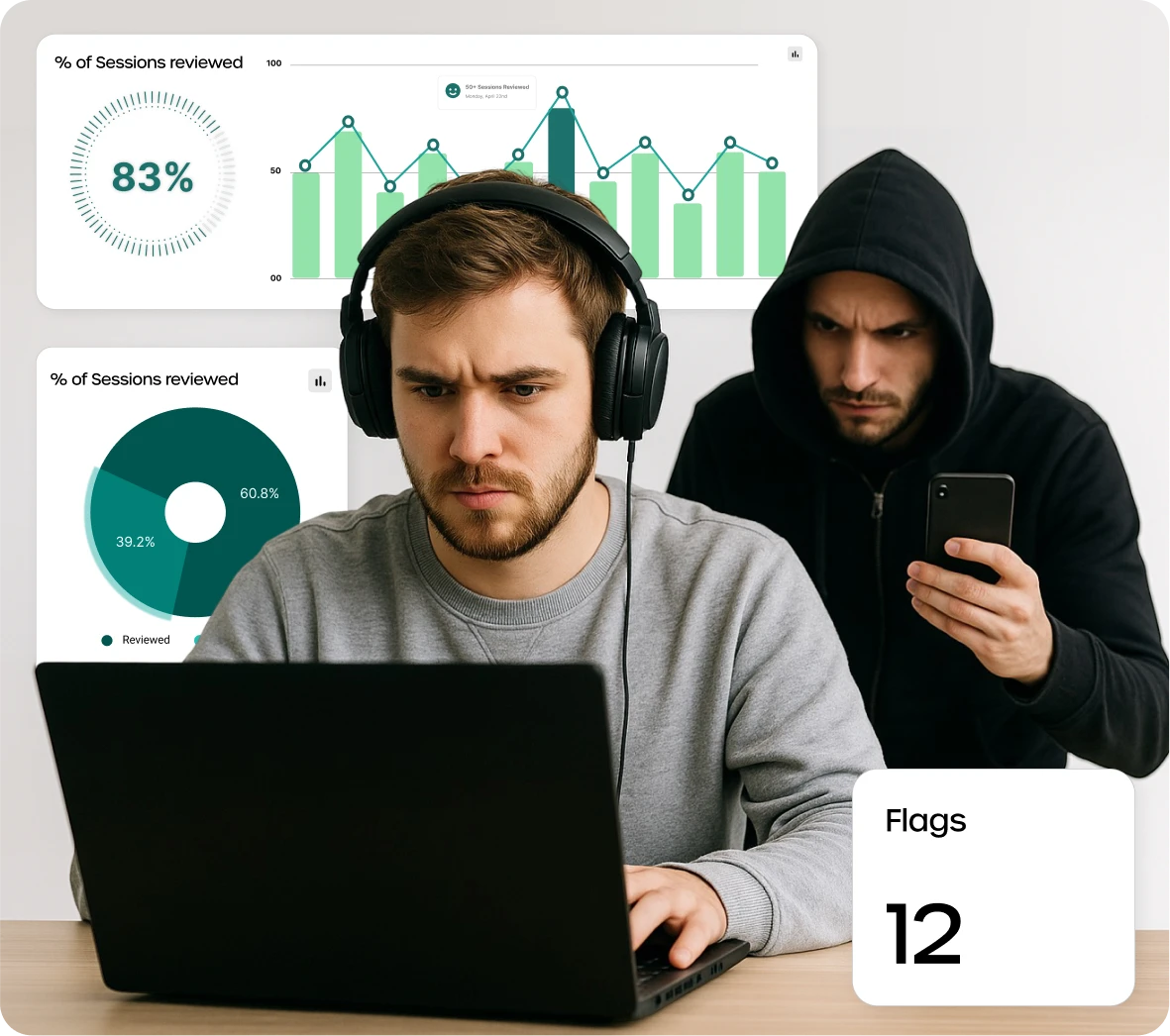
Securing claims & customer IDs
Agents using hybrid setups made it difficult to prevent screen captures, insider threats, and exfiltration of sensitive documents like ID proofs and claims forms.
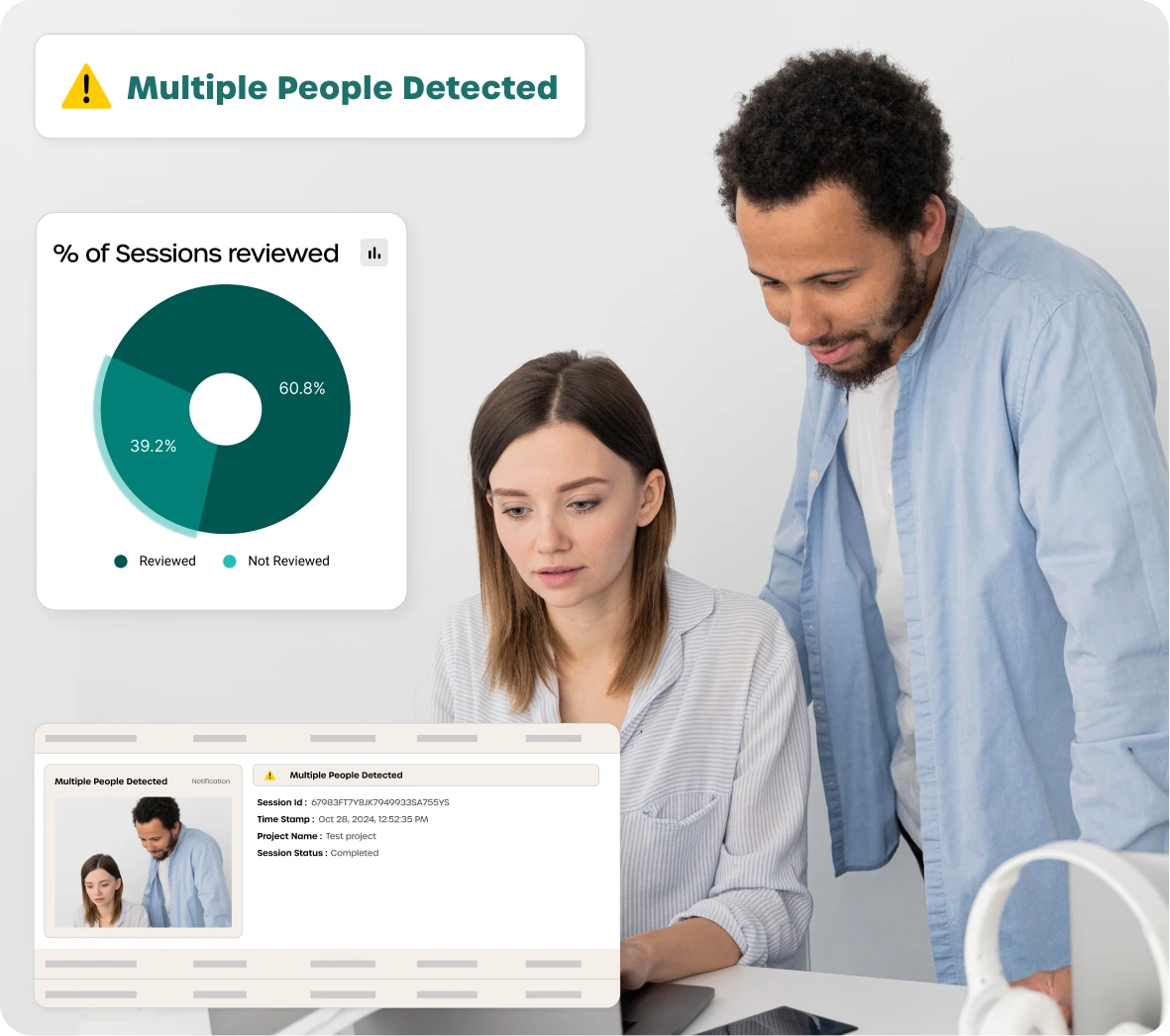
Securing code, algorithms & IP
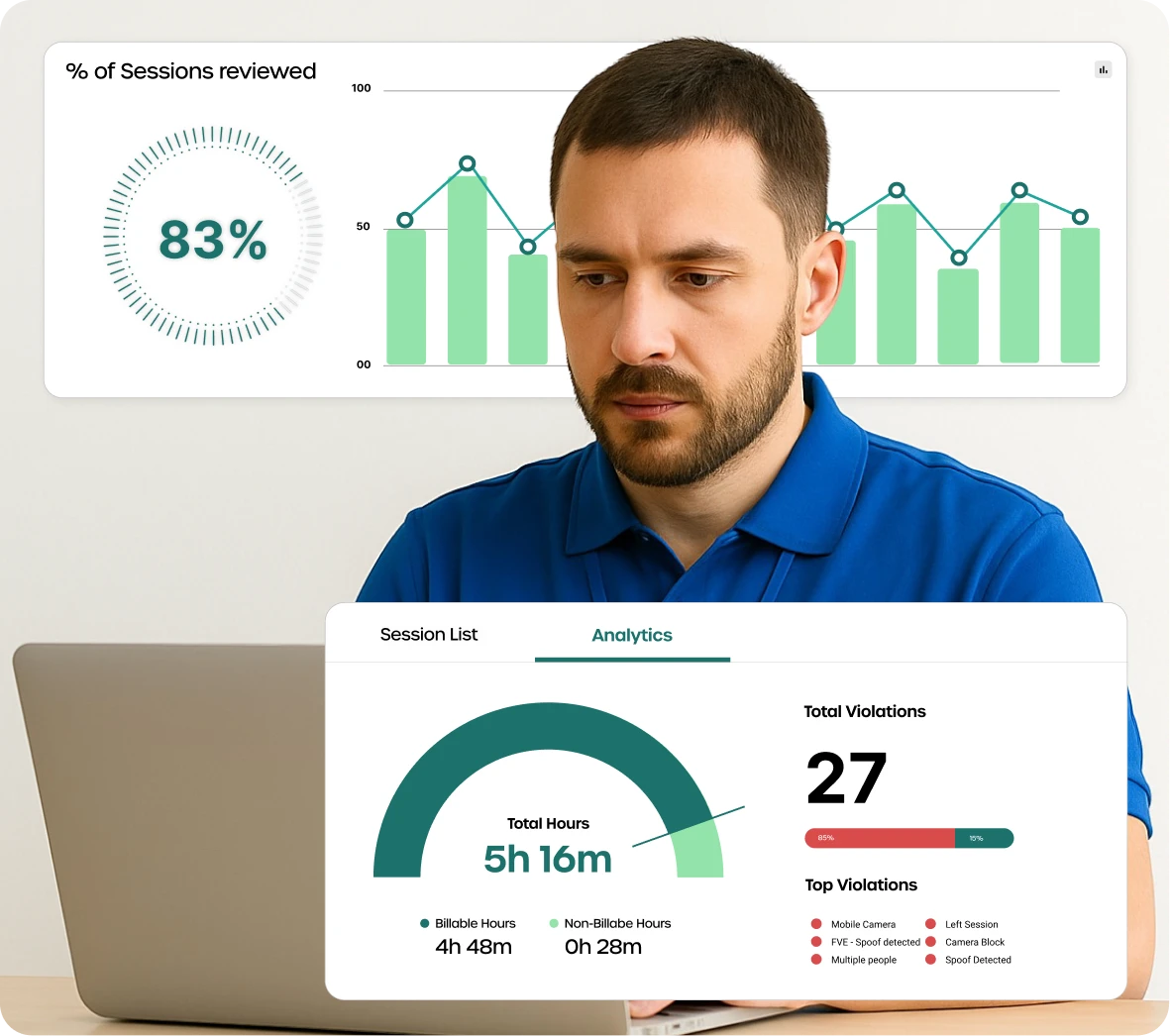
he client collaborated with global developers and needed to monitor code access, prevent GitHub leaks, and control IP movement across devices.
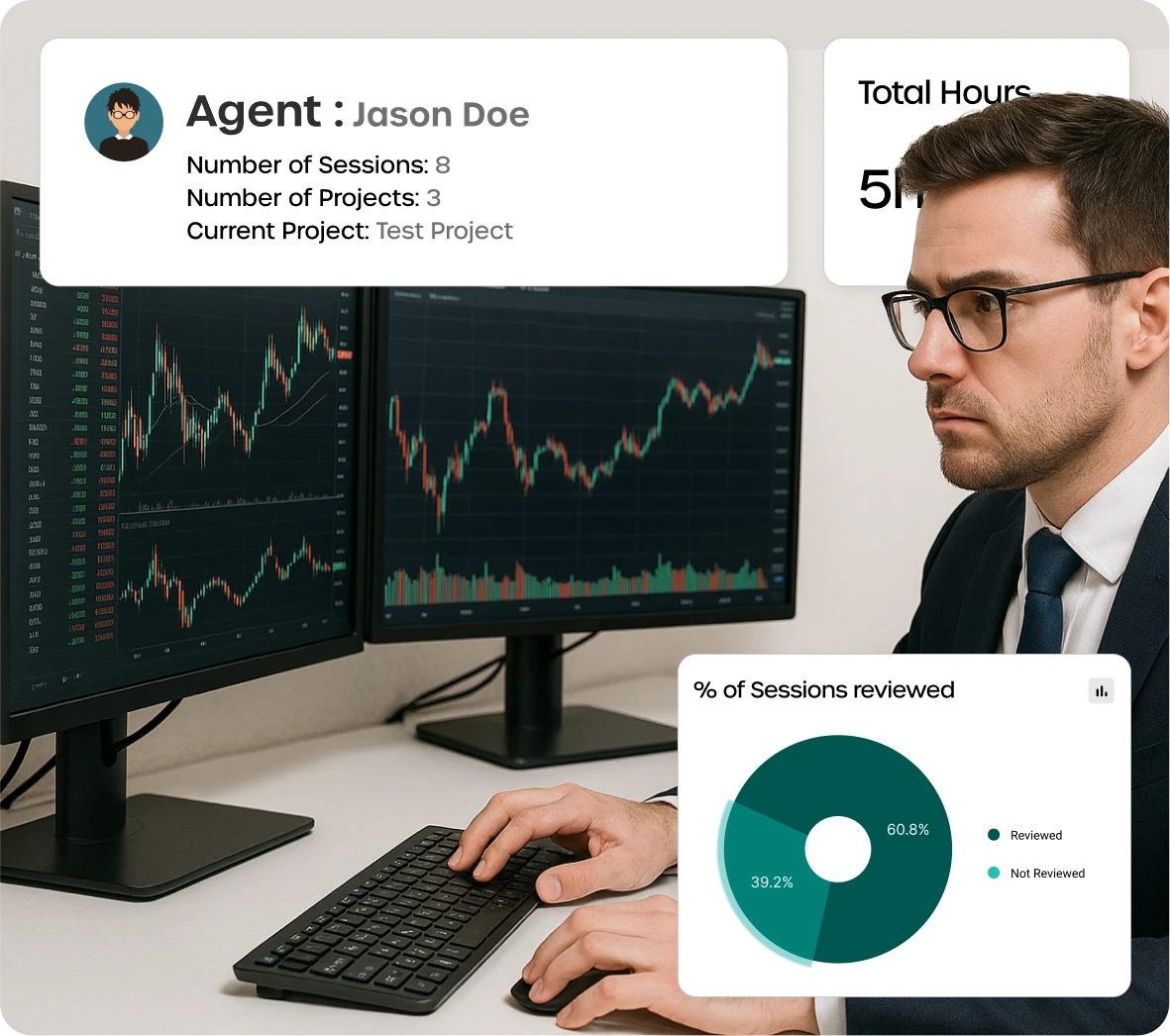
Protecting buyer & loan documents
With brokers using personal devices, the firm faced risks in securing loan applications, KYC details, and financial data—especially under AML and GLBA compliance.
Know More
Frequently asked questions
Everything you need to know about the product and billing.
-
1. What platforms are supported?
Windows and macOS. Deploy in cloud, on-premises, or hybrid models.
-
2. Is employee or biometric data stored?
For Secure eDLP, we store biometric baseline images and violation evidence images.
-
3. Will this impact system performance?
Not at all. The agent is optimized for low resource use and runs silently.
-
4. Can policies be role-based?
Yes. Rules can be customized per user, department, or project.
-
5. How fast is deployment?
It takes minutes per endpoint, with RemoteDesk support for onboarding.
-
6. What types of risks can it detect?
Identity verification and Authenticity, Authorized presence detection, Shoulder surfing , Mobile device usage, Cam block, identity spoofing, etc
-
7. How does it help with compliance?
Provides full session logs, alerts, and evidence trails for audit-readiness.
-
8. Does it integrate with other security tools?
Yes. It works with SIEM platforms, identity access management, and more.
Still have questions?
Can’t find the answer you’re looking for? Please connect with our team.



